How do we identify the devices on our network? How do we know whether an endpoint is a PC, an IP Camera, or an MRI machine? And how do we know if that device is authorized to access the network, and what it can access? I recently sat down with senior technical marketing engineer Krishnan Thiruvengadam to discuss how Cisco’s AI Endpoint Analytics (EA) can help.
For many years now, we’ve been using protocols like 802.1x to identify who is logging in to our network and what policy should be applied to our users. 802.1x works great, but it requires a piece of software called a supplicant on the end device. However, we’ve experienced an explosion of IOT devices on our networks in recent years, as cameras, badge readers, and apparently even fish tanks become IP-enabled and network-connected. These devices usually do not run 802.1x, but we still need to identify them and apply the appropriate security policy.
Manufacturer Usage Description (MUD) is a promising protocol that will help identify these IOT endpoints, but it’s not widely implemented. What’s needed is a way to identify endpoint types, based passively on the traffic they emit. This is where Endpoint Analytics comes in.
Using Deep Packet Inspection (DPI) on Catalyst 9000-series switches, Cisco DNA Center is able to classify endpoints based on four key identifiers: Device Type, Hardware Model, Operating System, and Hardware Manufacturer. For customers without Catalyst 9k, a Traffic Telemetry Appliance (TTA) is another option to collect this data.
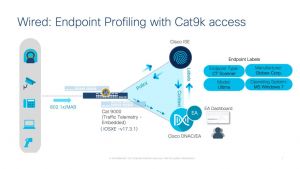
I think any enterprise needs EA, but a couple key use cases spring to mind. First of all, as we return to our office buildings, there are going to be new devices on our networks. We all know that our facilities teams have taken advantage of the empty buildings to add new systems which may be IP-connected. With users coming back in the office, we need EA to secure the network.
Health care is another great example of how critical EA can be. A hospital needs to correctly identify CT scanners, heart monitors, and other connected medical devices. Securing these devices could save lives.
Be sure to spend a few minutes watching my Coffee with TMEs interview with Krishnan, to learn about EA and what it can do for you!











