To keep pace with today’s digital transformation, your business strategy that propels cybersecurity is changing. And your teams are relentlessly working to keep your business secure while innovating to yield additional efficiencies and enhance productivity. A critical part of this journey is enabling a workforce to work securely on any device, anywhere, at any time. At the epicenter of this effort is the need to secure endpoints, seems pretty straightforward, right? If only!
The reality is that most organizations are dealing with continuing endpoint security challenges that are wearing them down. Now, some of this is self-induced by organizations adding multiple endpoint products, making endpoints extremely bloated and difficult to manage. Management complexities and product silos on the endpoint expose the fractures in the security armor which attackers readily exploit. But lets for a moment imagine that there is a reasonable number of endpoint products deployed; there are still some fundamental operational challenges that exist.
- Time: most organizations do not have enough time to go after every new threat, alert, patch, or compromised device accessing critical apps.
- Expertise: most security operation managers will state unequivocally that their teams cannot be experts on every threat, threat hunting while keeping up with compliance and privacy mandates.
- Evidence: organizations are sometimes challenged to get to the root cause of every attack, identify stolen credentials, or find the best security/productivity balance.
Now, we know that the main driver for customers’ endpoint strategy is to improve operational efficiency. So, the question that remains is, how do you tackle this? How can this be achieved in an environment where there is a huge shortage of skilled resources, with 74% of organizations saying that cybersecurity skills shortage has impacted their organization. Throwing people at the problem is not going to be the easy button to solve the endpoint operational challenge, and deploying more technology on the endpoint…not really. So what is left to do?
It is time to rethink the approach to endpoint security.
Rethinking the approach to securing endpoints
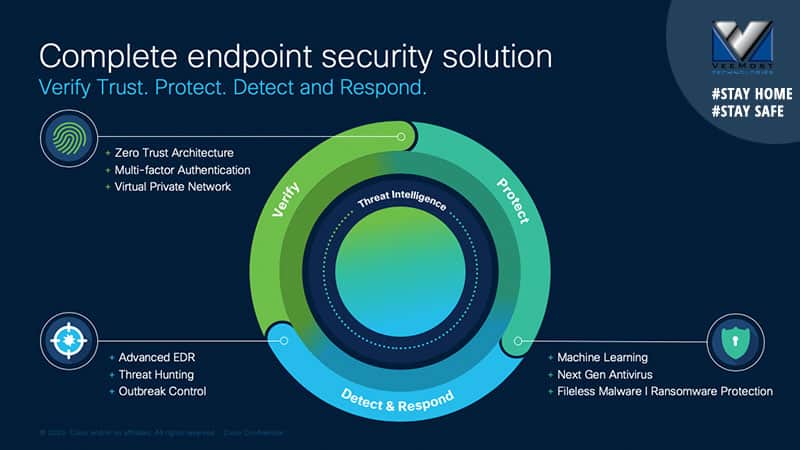
The first step in this journey is to broaden the lens beyond the traditional paradigm of endpoint security that covers protection, detection, and response. These are major critical capabilities for sure, but there is a pivotal part missing, verification that establishes secure and trusted access. Essentially, making sure that only good guys are let in. This critical function needs to be integrated with the traditional protection, detection, and response paradigm, without relying on additional agents. A true endpoint security solution must unify and automate the defenses to secure your users and the devices they use to access critical applications, but most endpoint security tools rely on yet more “agents” to deliver these capabilities.
Cisco Endpoint Security is the industry’s first solution that unifies user access and device protection. Cisco makes it easy to establish protection, detection, response, and access coverage across every threat to your endpoints. This is a holistic approach to security that works together on the endpoint – building an effective user and device control point for any organization to protect the workforce on any device, anytime, anywhere.
The proof is in the platform
Streamlining the endpoint solution will definitely help with the key operational challenges of time, expertise, and evidence, but even that is absolutely not enough. Hypothetically speaking, even with the most effective and optimized control points (i.e., endpoint, network, cloud, etc.), many of these operational challenges will still remain, despite improvements. Ultimately, customers remain challenged with siloed visibility, manual workflows, and complex integrations across their security estate. Ask yourself this question: Is it easy to investigate a threat completely? We did (and we do every day). In a recent study, the CISO Benchmark Study, where only 33% of respondents said it was easy to determine the scope of a compromise, contain it, and remediate from exploits. 33%!!!
To drive operational efficiency and improve efficacy, security platforms have entered into the picture. This is a welcome solution, as a platform will unify visibility, enable automation, and strengthen security across control points such as endpoint, network, cloud, etc. Aaah! Do you feel your shoulders relaxing?
Cisco announced the Cisco SecureX at RSA 2020. Cisco SecureX connects the breadth of Cisco’s integrated security portfolio with the customer’s entire security infrastructure for a consistent experience that unifies visibility, enables automation, and strengthens security across network, endpoint, cloud, and applications. So why does it matter? SecureX will deliver more context, analytics, and response to enable faster and better decisions.
SecureX builds the “mortar” into Cisco Security to deliver desirable outcomes for your endpoint security integrated with the Cisco Security portfolio powered by the platform. This means you can “amp up” the endpoint security by better sharing context and being a part of workflows to help customers save time, improve productivity, and clarifying insights with strengthened security. Simply put, implementing with Cisco SecureX together with Cisco Endpoint Security, endpoint events are enriched with actionable insights generated from either Cisco solutions or 3rd party solutions to accelerate threat detection and response. So, what does this mean for your endpoint security outcomes? Here is what you can do.
- Streamline threat investigations with Threat Response integration to reduce incident response lifecycle. This is saving time with the glue that pulls everything together, investigation, and action within a single console, and we have seen time to respond and remediate an attack go from 32 minutes down to 5 minutes. That is 85% faster!!!
- Realize fuller view of the threat landscape with SecureX which is critical to effectively accommodating a rapidly increasing remote workforce. The combination of endpoint telemetry with an expanded set of security telemetry provides context across your environment to dramatically reduce the attack surface on and off-network.
- Automate response actions such as host isolation or perform bulk isolation to immediately quarantine compromised endpoints.
- Cisco Endpoint Security provides SecureX with the ability to run automated playbooks and perform complex queries across all endpoints for forensic information and malware artifacts. This will simplify and accelerate threat hunting, incident investigations, remediation, and vulnerability | compliance assessments.
- With Cisco Endpoint Security, SecureX will have an endpoint security solution that uses a multi-layered protection capability with several proactive protection engines (machine learning, exploit prevention, file reputation, antivirus, and more) to keep advanced threats from compromising your endpoints. And what is more is that Cisco Endpoint Security provides retrospective security, advanced search and investigations, and human-driven hunts across your environment – to dramatically reduce the attack surface.
So, the next time someone asks you if it’s easy to investigate a threat completely, you can say, “Yes!”.
Sign up for SecureX
Cisco Endpoint Security together with SecureX is like peanut butter and jelly – it just goes so well together – more context, analytics, and response capabilities. Your endpoint security operational inefficiencies will be gone. The SecureX platform will continue to evolve so your security can keep up with the speed of business, and your business can keep taking new leaps.
SecureX will be generally available in June.
Source: blogs.cisco.com Credit@ Joakim Lialias